Zero Trust & Identity: The Number One Priority in Your Zero Trust Strategy
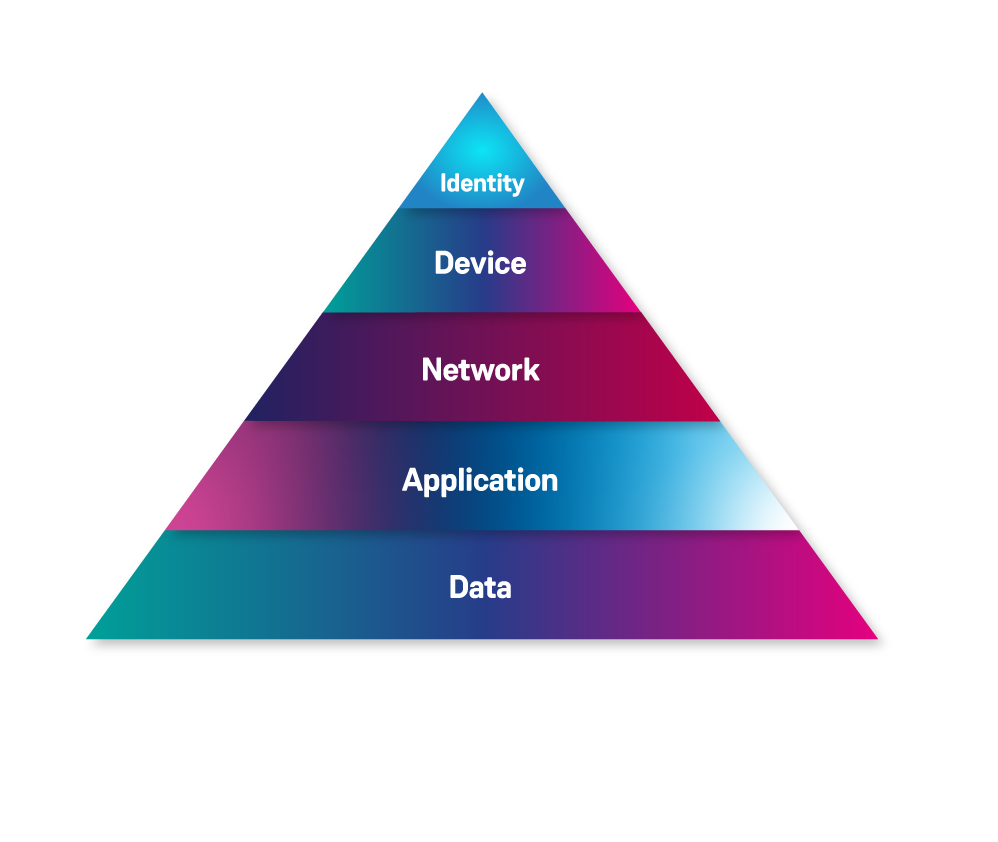
There are five core pillars of zero trust frameworks: Identity, Device, Network, Application Workload, and Data. All five of these pillars have a complete level of importance when it comes to implementing highly secure solutions and practices throughout an organisation and is always an insightful topic when in conversation with our customers. However one of those pillars is always at the forefront of the discourse both in customer conversations and in the wider cybersecurity industry—Identity.
Identity—and the attack vector it protects—directly impacts all of the remaining pillars, it is widely considered by experts as the most important priority when formulating a zero trust strategy or set of controls.
In this blog we’ll explore why designing and implementing a wide range of intelligent and pro-active zero trust based identity controls into your organisation can both protect from newly emerging threats aimed at identities, and set a strong foundation to assist with striving for further zero trust controls across the remaining pillars in the framework.
Why Identity Should be at the Forefront of any Zero Trust Strategy
Before explaining why identity defences should be the first thought on a zero trust agenda, it’s vital to understand what an identity was in the previous era of information technology and compared to now.
Traditionally, before cloud computing transformed into the mainstream that we know today, businesses and their IT estates were primarily based on-premises either internally or externally via a colocation data centre. Because of this, services were rarely public facing and identity controls such as employee user accounts were essentially ring-fenced within the company facility and not exposed to the multitude of threats that identities now face. The now archaic authentication method of username and password—that we in the world of security disapprovingly shake our heads at—was the norm as a result of this internal ring-fencing and the real attack vector that was given priority was the IP address.
Fast forward to 2023 with the traditional perimeter of private cloud being in the minority for most businesses, the IP address is still an important component to protect. However with native software defined networking and protection in cloud platforms today, it is no longer the singular bullseye for attackers. Recently explaining their own approach to zero trust architecture whilst building their own exciting ecosystem, HashiCorp described identities as the new IP addresses. As a result of infrastructure and data naturally spreading its wings into public cloud, the mechanisms for accessing those resources are now also organically at the front door of most organisations’ digital estates.
This is Sparta! Identity at the Front of the Phalanx
If you appreciate both film comparisons and security—King Leonidas of Sparta (seen in the brilliant film “300”) led his small but mighty phalanx of warriors against legions of enemies. When it comes to security, Leonidas is your sophisticated set of contextual zero trust identity controls and the legions of enemies charging towards him are the many attackers in the world now using tactics such as MFA burnout and advanced phishing techniques (to name only a few) to find a gap in that stalwart formation.
This new position that identity possesses in terms of priority for both threat exposure and the need for rigorous protection highlights the reason why it is at the front of both the zero trust and defence in depth frameworks. And to reaffirm the importance of this pillar, identity now plays the vital role of the leader in the phalanx of any zero trust strategy or roadmap for business globally.
Understanding Your Identities
It’s imperative that when you begin your concept planning for a zero trust strategy that all of the pillars are fully understood in the real world. As every business has different flavours of architecture, use-cases and controls, identity is no different with this regard. Understanding where identities reside across your enterprise and how they are controlled is vital for effective guardrail planning, because with the uptake of sprawled Software as a Service (SaaS) models, identities are likely spread across the organisation and potentially not managed under one unified directory or identity provider.
For example, Contoso who are striving for zero trust controls, have a central Azure Active Directory connected to an on-premises Active Directory (AD) environment to manage all identities and controls within the business that they’re aware of. When I mean aware of, it turns out that out of the visibility of system and security engineers, both the HR department and Finance department via shadow IT have each onboarded new SaaS based applications for the intent of deploying them into their business functions. These separated applications with business sensitive data have their own identity stores, credential sets and controls that are disconnected from the common directory and separated from the control plane of system and security engineers. With the correct controls and service connections these applications can likely be integrated into Azure AD and have Single Sign On (SSO), context controls and appropriate monitoring which can then be integrated into Contoso’s zero trust strategy.
However without that knowledge and asset management of these external applications, Contoso has potentially insecure and exposed identities that open a gateway into business critical data, all without the visibility. It’s vital that all of these past, present and future scenarios for Contoso identities are mapped out and understood so appropriate controls can be implemented to both improve the zero trust capabilities of the business and make a strong start to the zero trust adoption path that it is embarking on.
Everything Explicit, Nothing Implicit
The core thinking around zero trust architecture is to never implicitly trust an identity or resource within a workflow, even when those objects were trusted previously. The National Institute of Standards and Technology (NIST) phrase zero trust as not granting a trust based on their physical location or device ownership within an environment but Microsoft delicately paraphrase it to the term “Never Trust, always verify” that that paraphrased statement should be the foundation for all identity use-case mapping, control mapping and user adoption stories.
In the previous era of identity security, as long as an end-user had a username and password that were valid within the common directory that person would be both authenticated and authorised in one operation. Now the operation will indeed be longer to explicitly verify the users identity validity, but if designed and implemented correctly the user experience should not be altered to the point where it would hinder the user from doing their job and cause more overhead to the service desk. The user adoption journey for implementing zero trust based identity controls can be painful for both the IT team and the end-user if not planned correctly. However, if all of the identity scenarios and use-cases that I’ve discussed here are documented and understood within the wider IT, Security and adoption teams, then the location and velocity of these controls can be designed to suit any organisation and its users.
Contextual Control Coverage
Speaking to these controls, most of the mainstream identity providers such as Okta or Microsoft now have a wealth of security tooling and processes that have been designed from the ground up around zero trust architecture for organisations that have infrastructure and users distributed globally with no fixed office location, and need to adopt zero trust principles at pace.
As mentioned previously, the perimeter has changed with cloud-based distribution of users, endpoints and infrastructure which means controls have to adapt to intelligently analyse the context of where these resources are located, where they were previously located, do they have their security integrity intact or are they potentially compromised to name a few examples. Then, dependent on action policies after that context analysis, a set of guardrails need to be enforced on the identity to for example satisfy a multi-factor authentication prompt and ensure the identity context risk is deemed as low. The user would then be authenticated and then separated authorisation processes for access to sensitive data and applications can occur. This context-based approach to verifying a user’s identity validity does sound long and tedious to an end-user however, the user experience would be almost instant thanks to the speed that these controls activate. Providing a massive boost to identity security posture and getting closer to zero trust whilst impacting the user experience minimally is the win that we all should be striving towards when implementing this strategy across all five of the pillars.
In Summary
When consulting on zero trust strategy with customers I believe it’s always important to say that it can’t be achieved overnight and it is very much a journey of technical and procedural development across the organisation, along with the challenging task of gaining widespread user approval.
Implementing zero trust at the identity pillar can often be the most feared by security professionals as it’s the pillar that has the most direct interaction with end-users and their ability to do their day-to-day jobs, but that should be one of the primary reasons why it is so important to get right. Additionally because we now treat the identity with the same or perhaps more importance that we previously did with the IP address, investing in an ironclad strategy, set of tooling and upskilling staff on zero trust methods will guarantee a return on investment in terms of holistic business security.
Hopefully this article has highlighted the importance of beginning that zero trust journey in the correct manner by treating the identity pillar as the vital foundation and sharp edge of the security phalanx that has to be planned and implemented effectively to enable the remaining zero trust pillars to reach maximum success and security.